TLDR; – Encryption is important. Apple’s Advanced Data Protection is gone for only new users in the UK but existing ones keep it. You might not even had it turned on anyway. Regardless, your files are still encrypted. You can get round it if you change your country.
Just like the Joni Mitchell, Janet Jackson and Q-Tip song….. “You don’t know what you got till it’s gone”.
Encryption. The collection of mathematical primitives that allow us to keep our bank details from prying eyes. That allows us to upload photos of us, or our child’s first day at school, to an online cloud without fear of them being seen by other people we don’t want to provide access. That allows us to share passwords on the cloud so we can share with our iPhone and Mac. Rightly, or wrongly.
Encryption is fantastic. It’s the reason when you buy your new running shoes online someone can’t read your bank details. I don’t know if you’ve seen the result of someone inadvertently giving away a PIN or bank details to find their account cleaned out on payday. The subsequent panic when they realise they can’t pay their bills, can’t get their kids food, feeling utterly helpless. I have and I don’t wish that on anyone.
We often think of these things as not hurting because it’s digital, because it’s money, it’s not real. I’m here to attest the effects very much are real. When we see encryption being downgraded as any solution we should remember this story and another important fact for the cheap seats at the back…. YOU CAN’T SELECTIVELY DOWNGRADE ENCRYPTION TO JUST THE BAD PEOPLE!! WE ALL HAVE IT OR NONE OF US DO!!!!
Bad people are not fantastic. This is where encryption gets controversial. Sadly the same encryption used to store photos of your kid in their uniform starting their first day of school, is exactly the same kind that horrific child traffickers use to take disgusting photos of them and sometimes share with their sick mates. Obviously this is a highly emotive subject. My personal view, and I’m sure many share it, is if there was a way of decrypting when bad people used it but kept good people safe, then I would be all for it. Sadly there isn’t. It doesn’t matter if governments wish it so, if child protection groups demand it, if everyone, including myself, hopes for it. You either have encryption that protects everyone. Or you don’t. While some things are grey, encryption really is a binary choice (let’s not allow qubits to ruin a pithy remark!).
A lot of us in the tech and cybersecurity industry have hoped that successive UK governments would stop trying to break encryption. Sadly this government seems to have started where the last one left on this matter. It’s not a good place.
Talk of backdoors or weakening of ciphers so police can catch criminals sounds great and the media loves it. However they often forget to mention that this also allows criminals to capture your credit card numbers and CVV to then steal from you. It allows criminals to steal your private intimate photos you shared with a partner and blackmail you. You did nothing wrong. Why should you be at risk?
Also, it won’t stop horrific monsters doing horrific things. Not only do we lose our use of encryption for legitimate use, but we stop no one. Don’t believe me?
Let’s look at this article published in The Guardian a couple of years ago. A great piece by Shanti Das that makes the encryption problem pretty moot. Perverts are doing this in plain sight. When they create the “tribute” accounts over 14yo girls mentioned in the article there is no encryption. The photos are public. Instead of worrying about breaking encryption, might I suggest that the government instructs forces to reduce harms to children, by stopping what they see in plain sight first?! You don’t need laws to do that. The laws exist for them to track down people they think have committed a crime and arrest them. If people can see the crime because it’s on an unencrypted website then we don’t need to fuck up encryption for the police to act.
OK this wasn’t meant to be a rant about the encryption and the failure of successive UK governments to understand it. Back to the main point!
To E2E or not E2E, that is the question.
So hopefully by now we all agree encryption is a good idea. Hopefully some of us agree it’s rather brilliant. And hopefully some will also agree that trying to break it is futile and there are better ways to catch criminals.
There are even different flavours of encryption. The type that started this furore as explained by Zoe Kleinman in the BBC article, linked, is end-to-end encryption.
I think it’s important to understand that your data is still encrypted with Apple.
It’s not unencrypted. You are still protected. However, there may be chances that people can “listen-in” as your data is passing through the internet, or if they demand the key in a warrant, governments can decrypt your data. The Advanced Data Protection that Apple have removed, due to UK Government insisting on a backdoor that Apple didn’t want to provide thus removing the feature from the UK market, is end-to-end encryption. This type of encryption means that even Apple don’t have a key to your data, Only you do. As we’ll see later, setting it up means you have to create your own recovery key. If you lose this key you lose all your data. I think it’s fair to say this approach is not for everyone.
But should end-to-end encryption be for everyone? It’s only the police and governments that can force warrants right?! Keir Starmer only wants to go after the bad guys right?
Well let’s look at America. In particular the state of Nebraska in 2022 where a teen and her mother were arrested in an abortion related case. You might think (I don’t), that this “crime” warranted being snooped on and they should have been arrested. What if eating fruit was considered illegal but you like grapes. You then get arrested because you shared that in a private conversation? Keir Starmer won’t be PM forever. There might be be an authoritarian regime in charge. End-to-end encryption helps stop them coming after innocent people.
But the police are nice right?! I’m going to caveat this that I have friends that are police officers and I don’t think all of them are bad. That being said, the most horrific things have happened by the hands of police officers in recent years and I believe as an organisation they really need to look at that. Of these instances, the most well known is the murder of Sarah Everard by the police officer, Wayne Couzens, who had worked in various forces in his career. Imagine an officer as disgusting as this creep asking for a warrant to pursue a crime when he just wants to find his next victim. Until the police can root this out, I don’t think we should be trusting them with encryption backdoors or warrant demands to decrypt.
There is a popular fallacy, quoted by many various governments globally, that if you have nothing to hide you have nothing to fear. I hope this section explains how ridiculous that notion is and that good people need end-to-end encryption, to stop bad people in power abusing them and their privacy.
So what do we do now it’s gone?!?!
So hopefully by now (if you’re still reading) this ABSOLUTELY RIVETING article (right?!?) you understand that not only encryption is a wonderful thing, but end-to-end encryption is also wonderful and that us good law abiding people have a use case for both. Because sadly, due to poor vetting and people just ignoring things, we need to protect ourselves from bad people in power. A global phenomenon, not just a UK one. I also hope you agree that we would be better protecting children by actually acting on the things that are in plain sight first before we put everyone at risk by insisting on encryption backdoors.
So you might be lamenting the loss of Advanced Data Protection on your phone. Well, it’s not as easy as that. Anthonyhumphreysdev pointed out to me that if users already had it on then they still have it on. Many pointed out that if it’s not on they’re not missing anything (missing the point imho). My colleague, Gary Hunter, pointed out that his mobile was set to another country out the box so he also hadn’t lost Advanced Data Protection.
I recently moved from Android to iPhone. I’m also bit of an overly paranoid one so I just don’t use iCloud. I use a different end-to-end provider or don’t back things up to the cloud and use storage at home instead. Therefore, I don’t use Advanced Data Protection. But Gary’s comment got me thinking…. Could we circumvent this and turn it on now?
Less Ranting, more doing!
MASSIVE CAVEAT: ANYTHING YOU SEE BELOW THIS IS ME SCREWING AROUND. IF YOU CHOOSE TO DO THIS YOU DO SO AT YOUR OWN RISK. I CAN’T AND DON’T GUARANTEE IT’S SAFETY. I JUST WANTED TO FAFO!
So let’s add some data to iCloud, Oh interesting! Even though I didn’t think I used it, some text messages, passwords, and drive contents are there! Eek! Also my phone backed up to iCloud 2 days ago! I honestly didn’t know it was on but looks like some defaults are there!
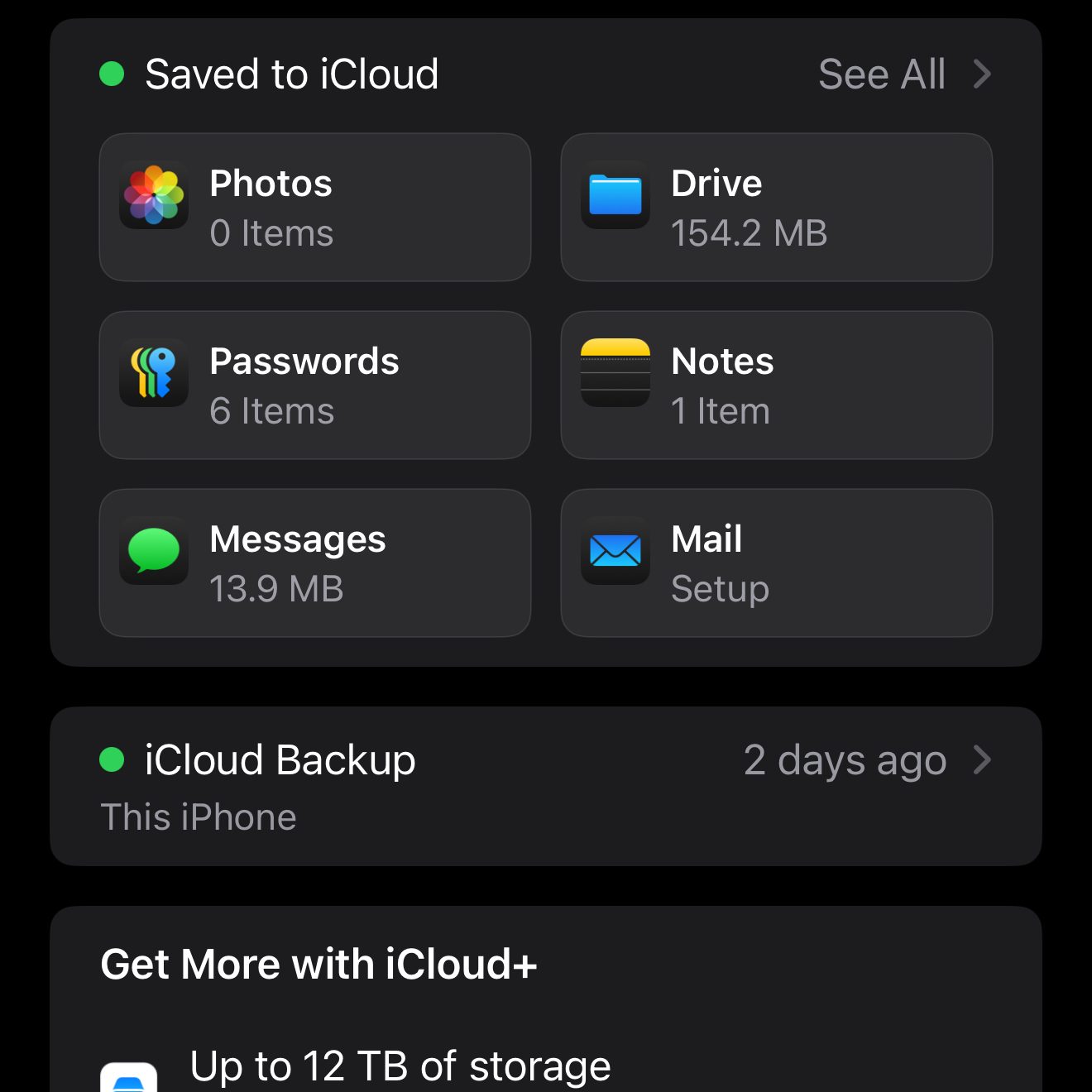
As we can see, Advanced Data Protection is off. I’m very intrigued by this “Access iCloud Data on the Web” feature. I’ll be turning that off, going forward!
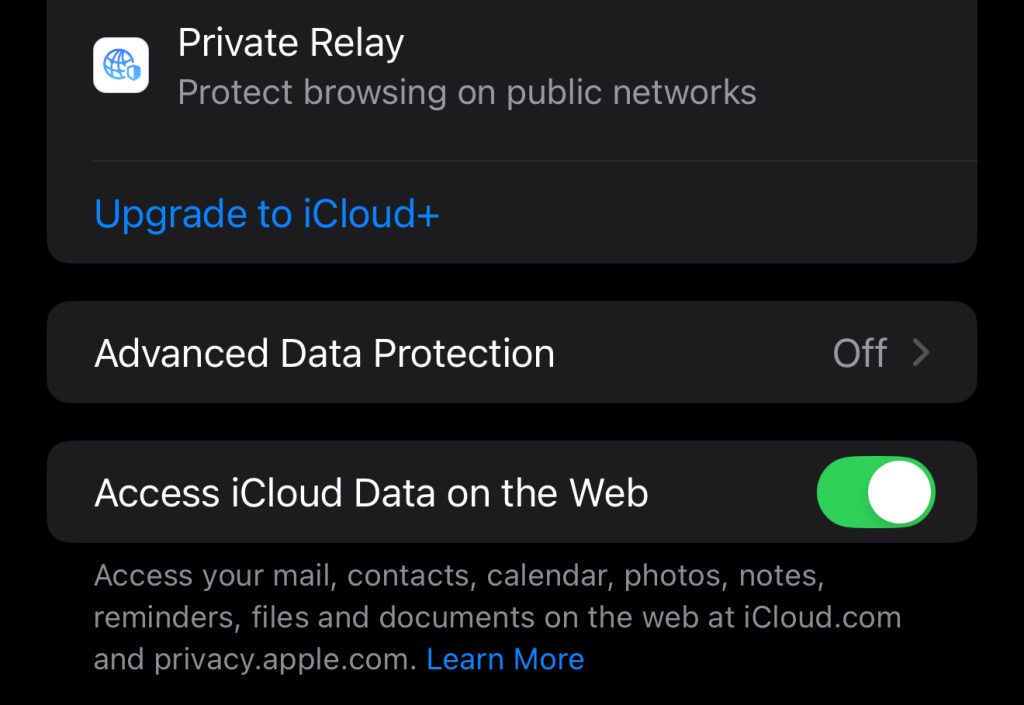
As we can see below, Advanced Data Protection cannot be turned on this phone as the country is registered to the UK. We can also see AnthonyHumphreysDev was right it’s only new users. The other thing to point out is that passwords, health data and maps data may already be end-to-end encrypted so you don’t need to do this. It would be wrong to think this doesn’t matter though. As stated, people upload photos of themselves for self-confidence, to share with partners, for perfectly legitimate reasons. Until every member of the police can be trusted and not just some of them, I don’t think they should be able to access photos of potentially law abiding citizens.

So that’s it right?! Nothing we can do! Might as well give up! Well not quite we can use the ultimate panacea for all our privacy problems! THE VPN!!!! This is of course, a joke. VPNs encrypt your data for sure, SOME can change your location, but actually there are other data points that may give away your location. A dear friend, Dan Card not only has an excellent blog in pwndefend, but his social media is littered with things that VPNs are crap for, among other quality destructions of cyber fallacies. Check it out. Don’t get me wrong, they have positives (encryption) but they’re not a panacea for every security problem. Nonetheless, of course I tried spinning up a secure core VPN that went through one location and then said I was in Belgium. Nope, I got told I’m still in the United Kingdom. Apple 1 – Dan 0.
So I then wondered how many things use location services on an iPhone. Quite a bloody few!!!!
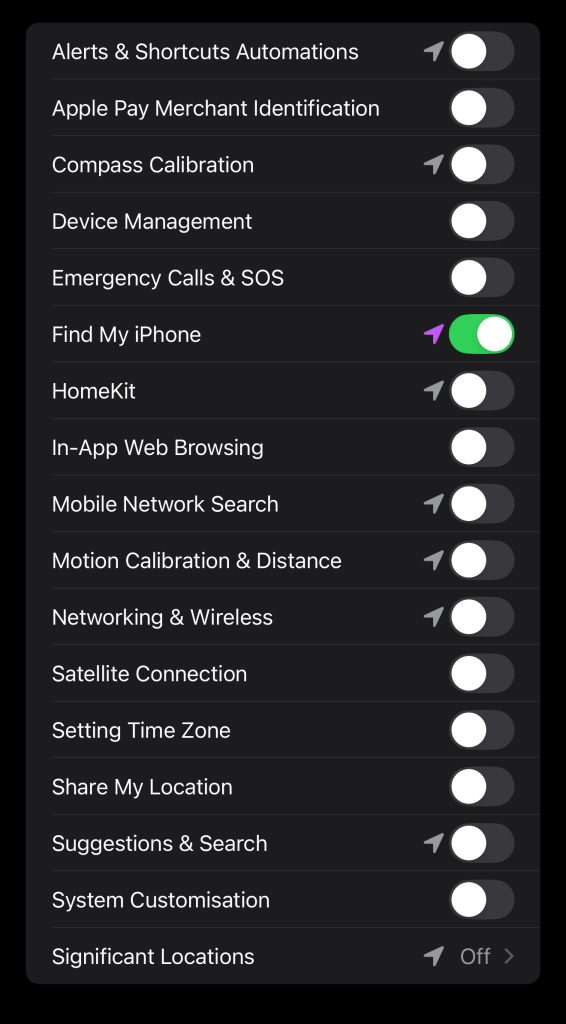
I turned them all off. I turned Location Services off completely! I also turned off Mobile Data in case GPS was giving away my location – goddam 5G!!!! (joke). I also disconnected the VPN and reconnected to Belgium via Mexico this time. Nope. De nada. Nothing. Still says I’m in the UK. Apple 2 – Dan 0.
So what super advanced tech could Apple be tracking me with?!? Pigeons?!? It’s gotta be pigeons! There’s a few by my window too. Maybe seagulls, the seaside mafia. They’ll ruffle anyone’s feathers for a chip!
Nope. It’s obviously my Apple ID.
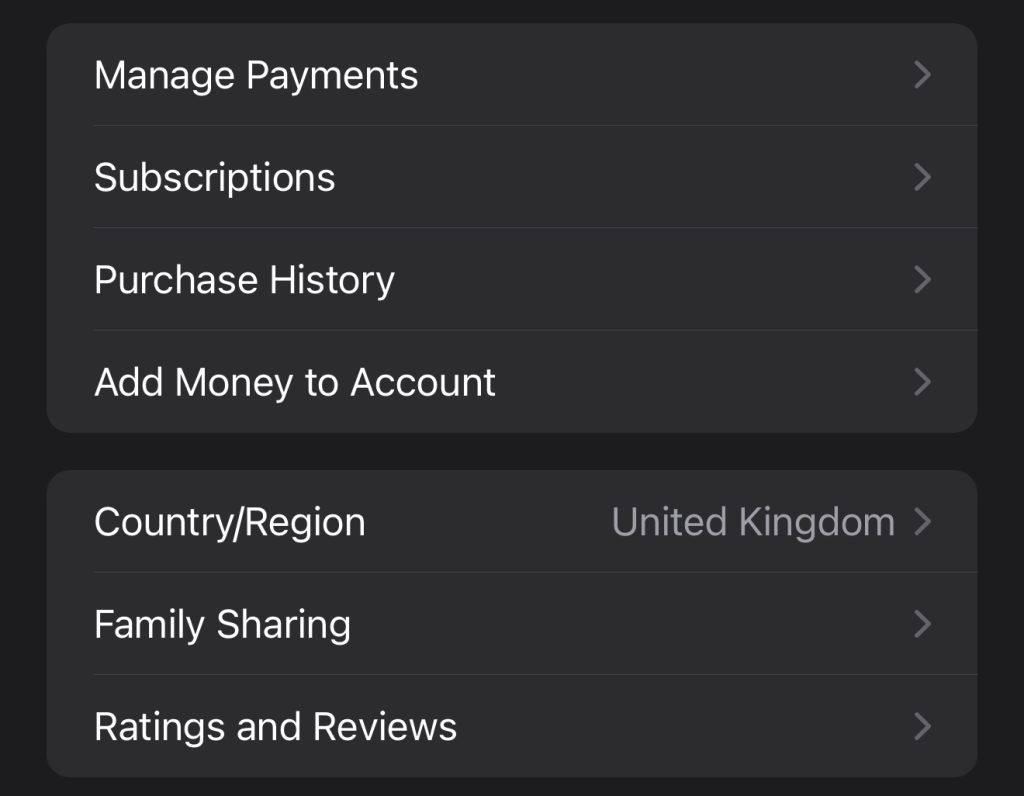
When you set up Apple ID you have to set up something to buy things with! So it knows I’m from the UK because of the country in sodding Media and Purchases settings!
Maybe it will let me just change my country…….NOPE! It asks you to have billing info for the country you want to change to through Apple Pay, Paypal, Credit / Debit card or something I’ve never heard of. Tried to change my Paypal address that didn’t work. Wouldn’t just accept my debit cards with a made up address (or my actual one) either.
Apple 3 – Dan 0.
But… after some mucking around we finally we able to change the country to Belgium! Some of you will know how I did it and it’s pretty easy to do tbh. It involves no technical skill at all. It’s not a hack 😀
If you can figure it out, great. If you can’t then that’s a thought experiment for you!
Apple 3 – Dan – 1 – about fucking time!!!
Let’s setup Advanced Data Protection….. or not. FFS.
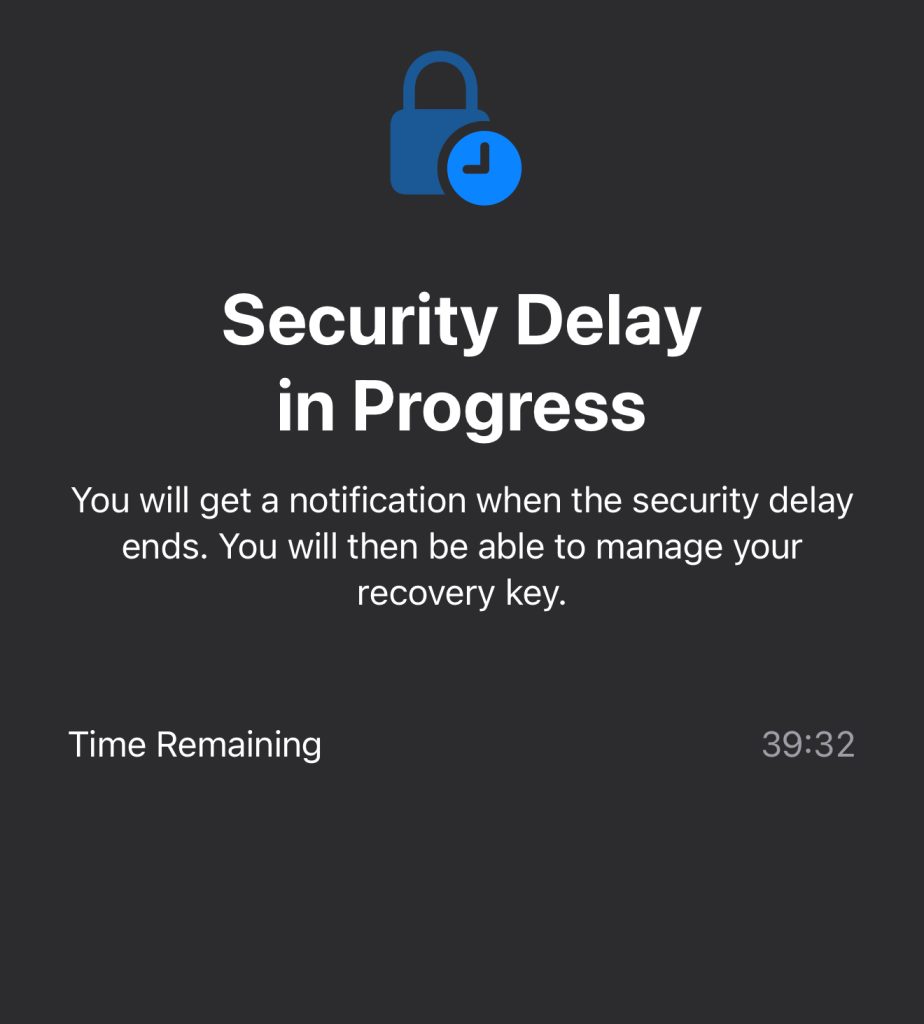
So getting the country to change forced a security delay of an hour. I guess I’ll grab a coffee and twiddle my thumbs. You don’t get a goal for that Apple, this is just a timeout.
So an hour later we come back! Hurrah! We can turn it on because I’m in Belgium! Go the EU!
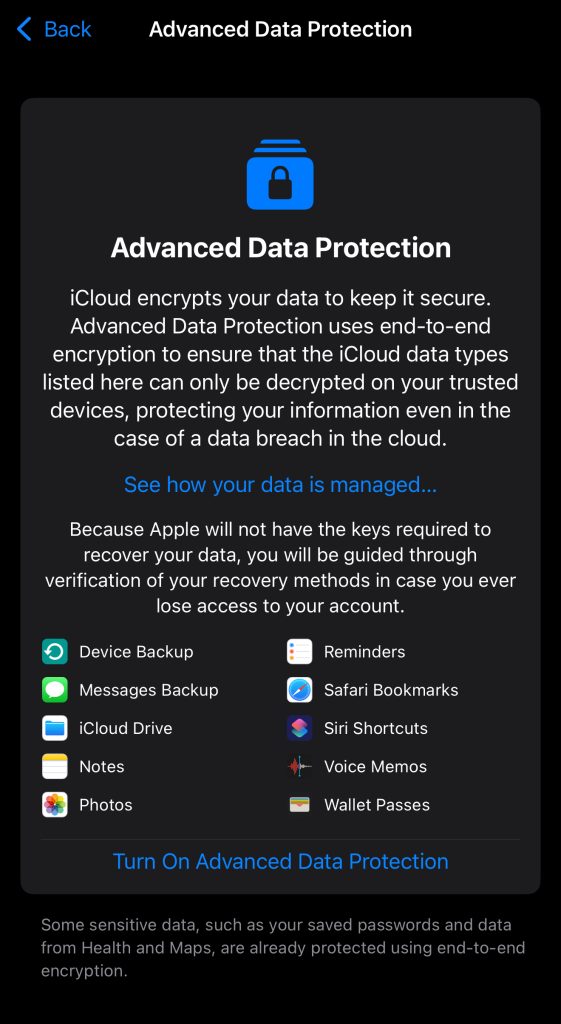
Apple 3 – Dan 2!
I then press the button, create my recovery key and then it turns on! I HAVE ADVANCED DATA PROTECTION!!!!
Apple 3 – Dan 3!!!!!
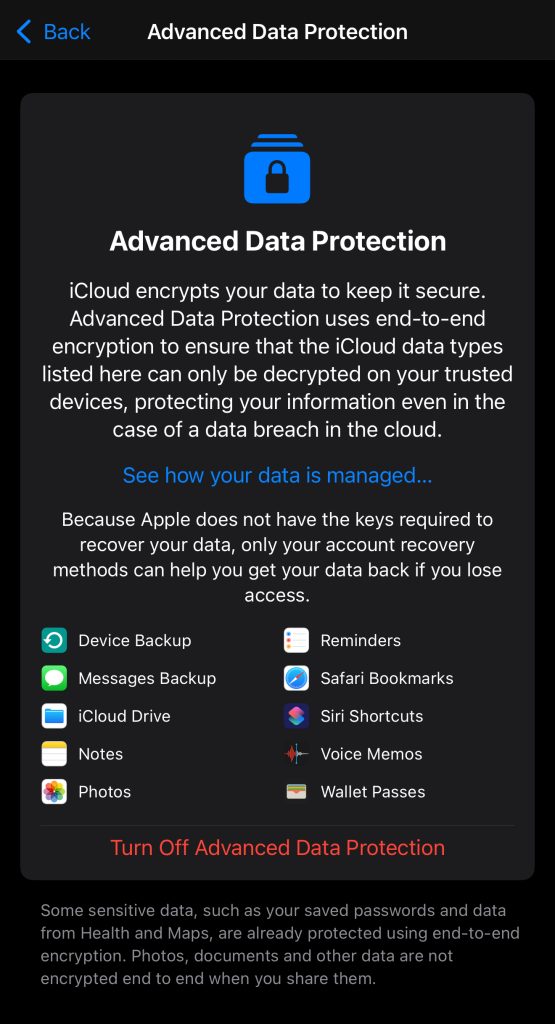
And then I backtrack my steps turn all the things I turned off back on etc etc and change my country back to the UK.
Why didn’t the score change?
So thats Apple 3 – Dan 4 right?!? We win right!?!
Well no. There are no winners in this charade. The government could well write a law that bans end-to-end encryption entirely. The government could ban encryption completely. That would be stupid, we can all see why, right?!
I hope our current PM, and subsequent ones see sense. I hope governments across the world, the US, the EU, where similar attempts to weaken encryption are being played out, see sense.
Hopefully we don’t have to keep telling people you can’t backdoor encryption and keep everyone safe. Please, enough now.
Leave a Reply