A review of the lockdown conference ConINT2020 and my first TraceLabs CTF
With COVID lockdown still very much a thing, combined with work increasing and just feeling as out of sorts as to be expected in a global pandemic, I’m struggling to keep going with my studies at Edinburgh Napier.
One outlet of fun and togetherness has been the Infosec community that I have got to meet (virtually) through my studies and continue chatting to online via Twitter, some Zoom chats like the fantastic Infosec Happy Hour created by The Beer Farmers and virtual cons! Previously in March, Stu Peck’s (cybersecstu) The Many Hats Club had put on IsolationCon as a way of bringing people together through virtual team tracks of Red Team, Blue Team and Purple Team. It was a great success followed by a super afterparty with YT Cracker on the decks!
Anyhow, I digress ( I will a lot in this blog, sorry it’s what I do (not sorry!))….. The Many Hats Club joined together with National Child Protection Task Force and Trace Labs, two organisations working to protect and find children and missing people through the use of Open Source Intelligence (OSINT) to help law enforcement in the UK, US, Canada and Australia/ New Zealand and ConINT 2020 raised money for these orgs. The talks were very much focussed on OSINT and had some of the best in the business. I watched transfixed on the awesome talks and I believe a lot are still up for watching if you wish to, I have included links for the ones I mention below.
First up I watched a fascinating opening keynote from
This followed a great talk from Alan O’ Reilly (AlanTheBlank) talking about Shodan for Beginners — it talk showed the awesome power of a really useful tool.
Tom Hocker (Human_Decoded) from Tracelabs then carried things on with a talk on OSINT ethics. It’s a very important subject and makes you remember that the people investigated have families, have people holding out hope that they’re still alive and it’s important to find information but to bear these innocent people in mind when conducting OSINT.
Next was probably the most impactful, important but harrowing talk I’ve ever watched from Nicole Beckwith (NicoleBeckwith) who drew from her experiences of working on her worst case (working for the police on a child abuse case), and also during her time volunteering for her local sheriff’s office, to explain about Mind Hacks — psychological profiling of subjects but also how to protect yourself and use coping techniques during and after investigations. I’ll be honest, I cried watching it and I still feel my eyes going as I think about it. I can’t imagine the pain and upset Nicole must have been going through during that investigation, but please do watch it.
After that I watched a really good tutorial on getting started in OSINT by Siobhan Kelleher (Secure_Coffee) that shows OSINT can be used across many business and personal use cases. I learnt a lot ready to prepare me for the CTF!
Finally, the awesome Bryan E. Hurd (Bryan_E_Hurd) ended the talks with a fascinating closing keynote on previous OSINT investigations in military and commerical environments and how visualisations can bring the story and narrative to bring out the facts. I remember him saying, “You bring the truth. Others bring opinion” which is a fantastic way of remembering exactly what OSINT is for.
That was the picks of that day but I spent quite some time catching up with all the talks once they were posted, all were brilliant and well worth a look — head to the ConINT YouTube playlist to watch them all!
So onwards to the CTF!
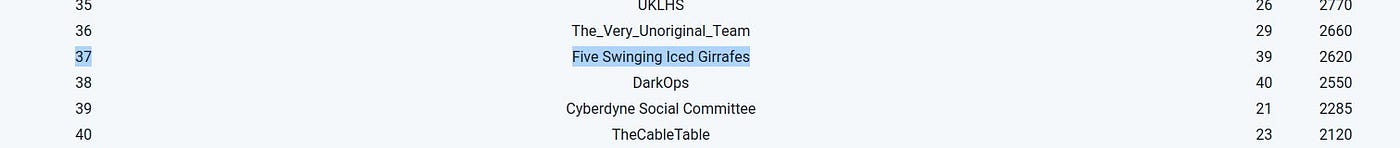
This was my first OSINT CTF and I teamed up with Atomic Maya and Kathryn (sudoKathryn) for our 1st CTF as the team Five Swinging Iced Girrafes! How did we come up with the name do you ask? Well we got the name from a random band name generator and chose music that we liked and then the name that we liked!
The team was put together very last minute so we had no time to work together as a team before the CTF but we seemed to connect well and help each other on the way. I believe we were all rookies and this was our first one so we helped where we could and learned where we needed to.
I had done a little prep work beforehand based on the talks watched previously so was using sock accounts for the investigations, inside the Tracelabs OSINT VM wrapped round a VPN connection. I won’t go into much detail on this setup as that’s for another post but it is very good to get an environment prepared.
Once prepared we started! It was….. well quite slow and daunting, to be honest! I think it’s safe to say we all felt like deer in headlights at least for the first hour, if not the majority of the next four hours, but also that’s totally understandable!
We had our six missing people to find. It was actually quite chilling but also quite emotional to see them. These are real missing people. They have lives. They have families. One thing that I noticed is that although there were a mix of people, the majority of cases were female and of those a high proportion were under 18.
It’s quite worrying when you see that proportion, but also quite sickening when you think about their last seen locations and later the circumstances that lead to them going missing. Sure, some don’t want to be found but anecdotally, it seems that many are kidnapped. It’s difficult to not get emotive on it but the best way to help is to stay focused, compartmentalise like Nicole mentioned in her talk, and deal with facts objectively. That’s how they will be found.
I can’t go into further details as we should respect the privacy of these real people but in some places it was very hard hitting. Atomic Maya definitely pointed out some great techniques to myself and Kathryn (I think one got nominated for MVO (Most Valued OSINT, nice one!), and Kathryn found some awesome OSINT too. I focused on social media. Mainly Facebook, Instagram, LinkedIn and using a program called Sherlock to look for other potential username accounts to pivot and find more information.
If you can find a username of a missing person, you can then look for friends, some might not be relevant but some might actually be useful and provide further information. There might be a photo of the missing person showing a tattoo piercing not previously known about and this all means points in the CTF, but also good intel for law enforcement. The better the intel, the higher the points given and this then bases your team’s ranking. To be honest though, the ranking isn’t really that important, the important thing is getting information that may help these people get found.
So four hours passed like four minutes. Our judge wasn’t too chatty but approved most things. All in all we came 37th out of 125 teams! We were really happy with this, in fact I was ecstatic. It was a great effort and thanks to both Atomic Maya and Kathryn for being amazing team mates!
I remember leaving the experience and wanting to do this more often whether as part of a CTF or on a more serious voluntary basis. It was definitely an inspirational conference and CTF.
Leave a Reply